Security Policies
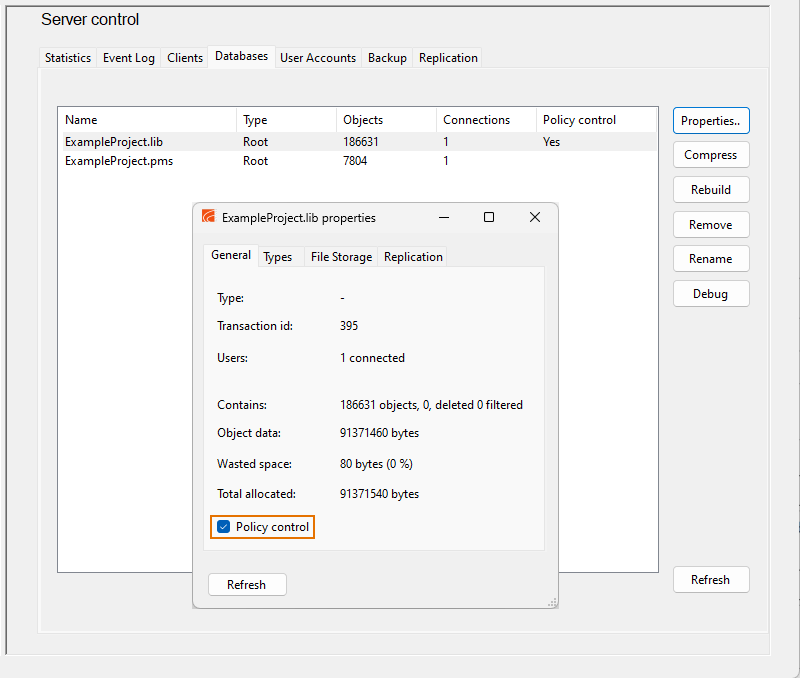
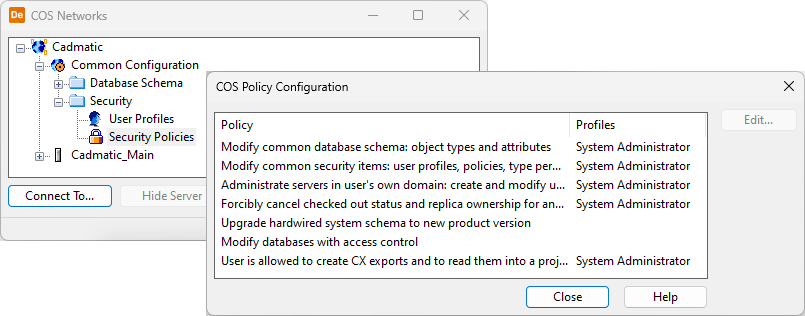
In the CADMATIC desktop, select Object > Manage COS and browse to [server] > Common Configuration > Security. Double-click Security Policies to control access to certain administrative operations by specifying which User Profiles are allowed to perform the operations.
|
Policy |
Details |
|---|---|
|
This policy enables defining object types and object type specific attributes. |
|
|
Modify common security items: user profiles, policies, type permissions |
This policy enables defining user profiles, security policies, and object type specific permissions. |
|
Administrate servers in user's own domain: create and modify user accounts; create, remove, backup and restore databases |
This policy enables defining user accounts and managing databases in the COS servers that are sharing the same user accounts. |
|
Forcibly cancel checked out status and replica ownership for any object |
This policy enables forcible canceling of object check-outs and taking or requesting object ownership from replica servers. Note: This policy is required for using the Debug Databases command. |
|
This policy is only needed when the software has been upgraded to a newer version and the project environment needs to be upgraded to be compatible with the new version. At other times we recommend this policy to be disabled. Note: Upgrading of schema cannot be undone except by restoring the old version from a backup that has been created with the old version. |
|
|
This policy enables reading, creating, modifying, and deleting objects in library and project databases that are using access control. User profiles that are not added to this policy are only able to read data from the database. Access control can be taken into use by enabling the Policy control option in the properties of the database. The option can only be set via the CADMATIC desktop command Manage COS Servers; it cannot be set via Manage COS. Note: To edit this security policy, your user profile must be included in the security policy Administrate servers in user's own domain: create and modify user accounts; create, remove, backup and restore databases. |
|
|
User is allowed to create CX exports and to read them into a project |
|
|
This policy enables defining Model Filters for replication. |
|
|
This policy enables defining which Content Categories to allow in the COS network. |
|
|
This policy enables creating, updating, and deleting fields and sub-tables in the SQL database of P&ID. |
Example security settings
A typical COS setup might include the following profiles:
System Administrator:
-
Everything allowed.
Project Administrator:
-
Can create and modify all objects; can remove some objects.
-
Schema modifications allowed.
Advanced User:
-
Can create, modify, and delete plant objects and documents.
-
Can create GDLs.
-
Can create and modify dimension tables, catalog parts.
User:
-
Can create, modify, and delete plant objects and documents.
-
Can create GDLs.
Subcontractor Administrator:
-
Can administrate local servers.
-
Otherwise like a User.
Thus, the policies would be:
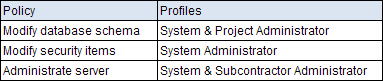
Note that although a subcontractor user may have the Satellite Administrator profile, the user does not have administrative rights to the main site's servers. This is because the policy gives access only to those servers that the user can sign into.
Here is an example of permissions for some library objects (e.g. GDL) in this environment: